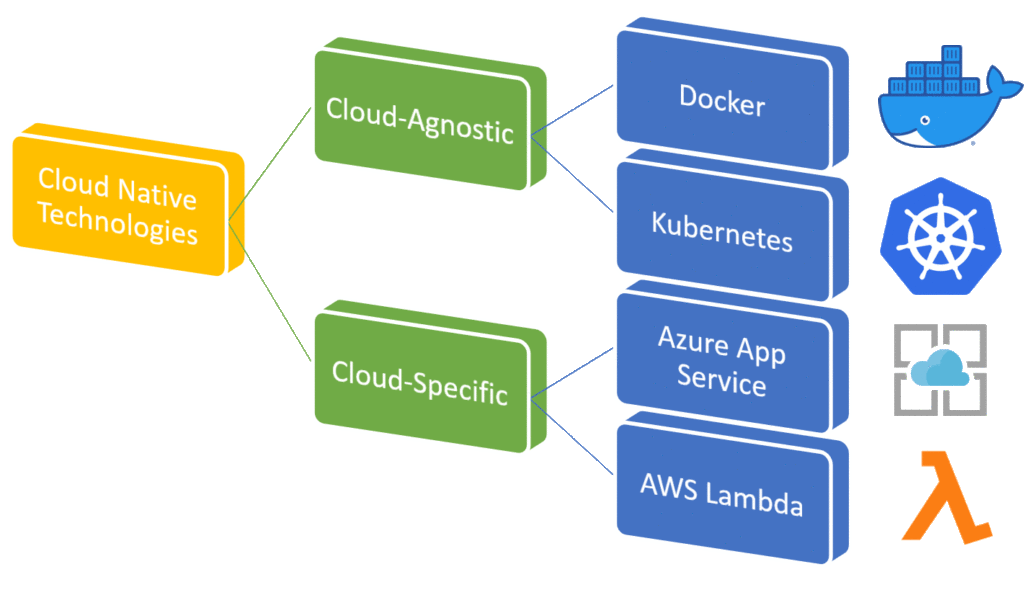
Cloud agnosticism – Part 3
Introduction
Many organizations are looking at cloud-agnosticism architectures to avoid vendor lock-in, whilst minimizing hosting expenditure and increasing availability and scalability according to demands. At the heart of cloud agnosticism lies the notion of multi-cloud environments. In this post, I will be discussing the existing literature pertaining to infrastructure as code, containerization, and leveraging a multi cloud setup towards the achievement of cloud agnosticism.
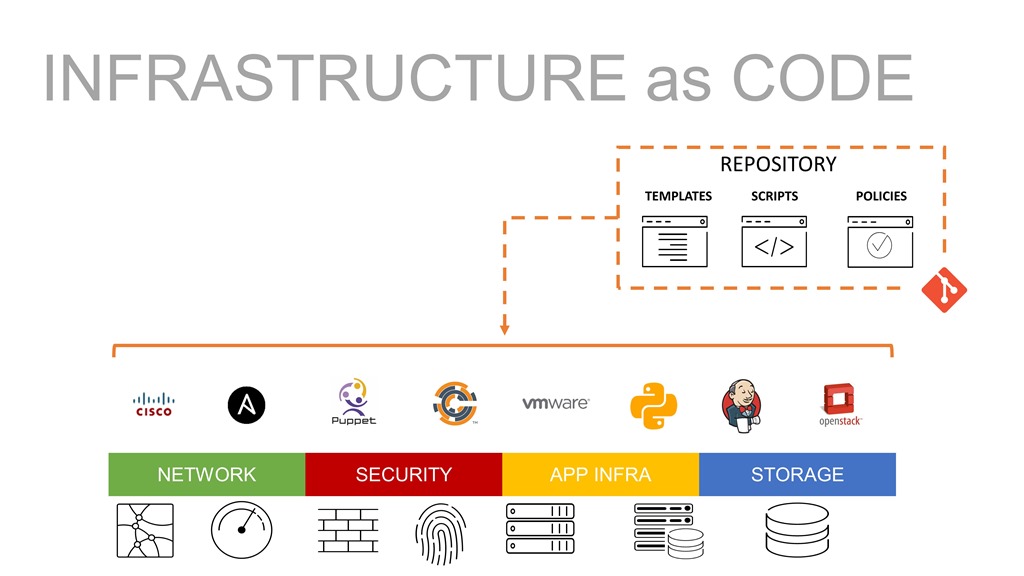
Infrastructure as Code
DevOps teams are responsible for the design, implementation and operations of cloud agnostic environments through IaaS, IaC and Containerization. The study by Patni (et al., 2020) utilized the templates provided by Azure Resource Manager (ARM) to deploy a web application using Terraform and Pulumi. The results demonstrate that the utilization of ARM templates increase the agility to deploy and manage the web application. This study aligns with the study by DesLauriers (et al., 2020) whereby templates are adequate in the provisioning of infrastructure. The major difference between these two models lies in the implementation, whereby Patni (et al., 2020) opted ARM templates which lead to Azure vendor-locking.
A cloud agnostic framework needs to incorporate a security-by-design approach, whereby minimal privileges is necessary towards a secure environment. The study conducted by Shimizu and Kanuka (2020) identified a security risk which needs to be mitigated when utilizing IaC on cloud platforms. Such risk is presented by the cloud IaC template, whereby permissions for each cloud service and cloud environment, must be managed by developers. Failure to properly manage such template may have adverse effect on the cloud architecture, especially in case of cyber-attacks. This study posited a framework to find the least privilege by testing on the cloud platform and reconfiguring the permissions. This model was evaluated using multiple case studies on AWS, whereby the results demonstrated that least privilege was determined within a reasonable amount of time. Furthermore, the model can reduce the number of tests compared to random and heuristics methods by 69.3% and 39.8% respectively, thus reducing time and cost effort to identify least privilege for IaC templates.
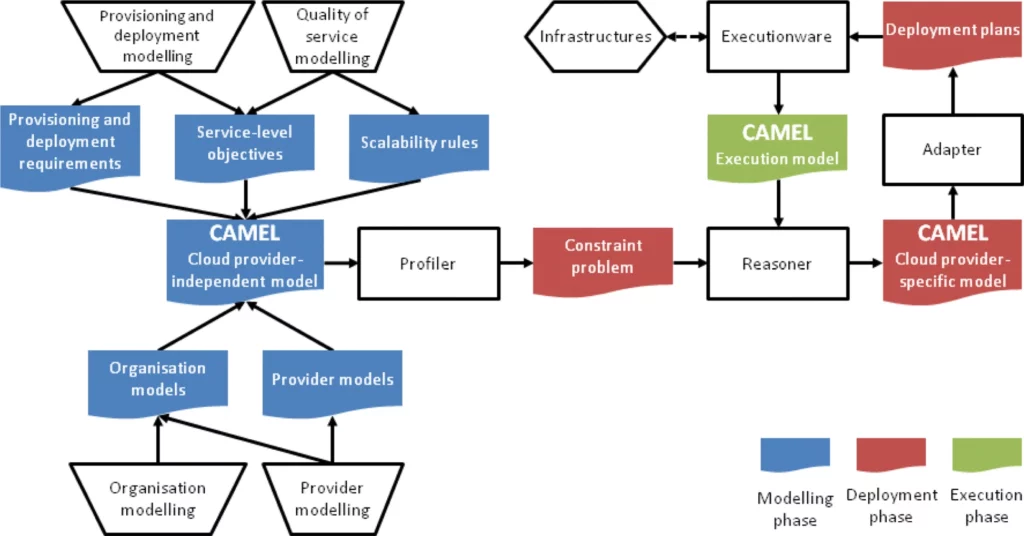
The study by Rios (et al., 2017) proposed a CAMEL-based (Cloud Application Modelling and Execution Language) security language for multi-cloud applications. This language addresses the lack of expressiveness in existing languages towards (a) automation of distributed deployment, (b) computation of SLAs, (c) risk analysis and service matchmaking of functional and security features. The MUSA framework is utilized to provide the necessary preventive and reactive security capabilities in a multi-cloud setting. MUSA is adopted by DevOps teams and introduces the notion of DevSecOps. This framework has been validated over multiple case studies including Lufthansa and Tampere University. This framework provides the mechanisms to the (a) replication of applications, (b) tier-partitioning of applications, (c) obfuscation of application logic and (d) partitioning of application data. The utilization of tools such as MUSA ensures that security considerations are addressed in the engineering of solutions in multi-cloud environments, thus ensuring reliability and protection.
Containerization
With the emergence of containerized technology, resource scheduling has been extensively researched. Containerization allows faster deployment and scaling, whilst ensuring immutability during replication or movement of services.
Organizations which are refactoring or redesigning their applications to leverage this technology are rewarded with increased elasticity and improved resource utilization. In the context of cloud agnosticism, such an approach provides organizations with the ability to run containerized applications on multiple CSPs. This study conducted by Li (et al., 2019) proposed a service performance-based dynamic provisioning approach in containerized cloud environments. Such approach attempts to address the unpredictability of business requirements in the dynamic provision of resources. The solution continuously gathers metrics from the applications to build customized scheduling strategies to improve availability and reliability. Challenges of service performance include (a) latency, (b) throughput, and (c) CPU and memory utilization. The study conducted experiments to evaluate this approach, whereby it is shown that dynamic scheduling can maintain a stable performance whilst improving the resource utilization of the cluster.
Distributed applications may also benefit from a multi-cloud environment. Organizations leveraging edge providers can offload certain microservices from the multi-cloud architecture to the Edge to improve performance. Several edge providers such as Microsoft Azure IoT Edge, Amazon Greengrass and IBM Edge Application manager, utilize a containerized approach for IoT. The study performed by Liu (et al., 2021) measured the performance of a microservice model using a vertical plant wall with various sensors connected to Azure Edge cloud. The microservices running in the edge container engine met the <200ms latency. This study demonstrates that splitting applications into small microservices allows relocation of such containers to various locations and platforms (cloud or edge), for increased elasticity and responsiveness.

OASIS TOSCA is a standard utilized in the declarative description of cloud applications. The adoption of such standard facilitates cloud portability of applications, using a cloud orchestration tool, MiCADO (Microservices-based Cloud Application-level Dynamic Orchestrator). The integration amongst TOSCA and MiCADO is achieved through the application description template which allows the creation of generic templates, thus achieving portability. This solution proposed by DesLauriers (et al., 2020) allows the provisioning of containers, virtual machines, and policies for a given application. A proof of concept using TOSCA-based templates in MiCADO has been undertaken for a Science Gateway in Sleep Healthcare. The results demonstrate that MiCADO facilitated the deployment of Infrastructure services (IaaS) and porting of a complex application from one CSP to another, with minimal changes to the original template. Orchestration for containers can also be implemented using TOSCA interfaces, thus allowing engineers to create a Docker Swarm or Kubernetes using the same template on different CSPs, with minimal changes. Furthermore, TOSCA-based templates in MiCADO allow user-defined auto-scaling, an important aspect in containerization.
The study conducted by Gholami (et al., 2020) explored an alternative cost-effective solution to meet the performance requirements by containers. Traditionally, when a container requires additional performance, the organizations need to scale up or out, thus increasing the cost. This study proposed a framework which utilizes multi-versioning for the resource-heavy containers using an open-source extension of the docker framework, specifically DockerMV. Multi-versioning allows a resource-heavy microservice to have multiple versions including a lightweight version (with less functionality) of some its essential components. Such approach allows the framework to determine whether to use the lightweight or heavyweight service. The study was validated through three experiments, using ideal, worst, and adaptive approaches. The results demonstrate that a multi-versioning approach meets performance requirements whilst retaining quality of services using the given resources. Such a proposition is relevant because it provides containerized applications running on multiple CSPs the ability to utilize their resources in a cost-efficient manner.
The study by Xia (et al., 2021) posited a model utilizing a Docker image repository management system to provision and control cloud resources. Such management includes (a) secure application hosting, (b) stable image building, (c) image authorization and (d) image distribution. The model was evaluated using an experiment consisting of an application server containing 3 distributed storages, 3 master nodes and 1 worker node. The results demonstrate that the efficiency of image pull and startup are dependent on the size of the cluster and image.
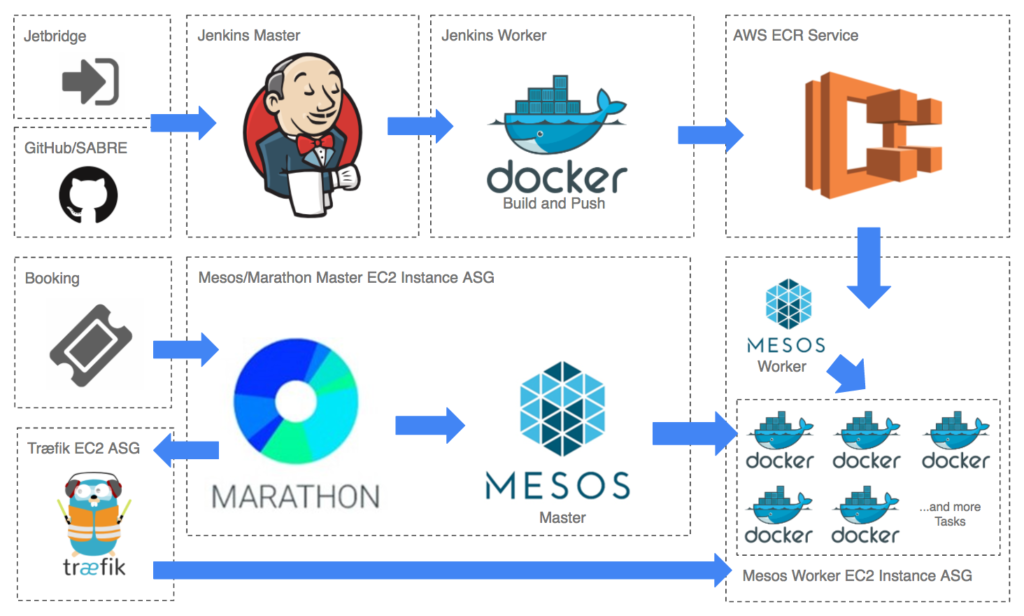
The containerized microservices approach contrasts with the traditional delivery in large Virtual Machines. The use of container orchestration tools such as Marathon allows users to achieve CI/CD as per DevOps methodologies. The study conducted by Ravula (2017) posited a framework to deploy immutable containerized microservices using tools such as Marathon, Docker, Terraform and Jenkins. This framework has been evaluated using a case study, whereby results show improved average release cycle, increased productivity, reduced infrastructure costs and reduced deployment failures. Such a model allows organizations to achieve Hyperscale computing. Furthermore, the study identified a reduction of 25-30% on AWS infrastructure costs through the adoption of containerization.
Conclusion
Cloud agnosticism provides organizations with the necessary support to implement industry standards and best practices, thus improving their DevOps processes and products (Bollen et al., 2018). Improvement to the product service delivery, positively affects products’ uptime, reliability, and functionality. Such gains are important for organizations and end users, since product disruptions or lack of functionality, reduce the customer experience and overall service offering. Specifically, reliability is an essential feature of any software as a service (SaaS) offering, whereby the community consumes such services as a commodity as required. These services include banking, entertainment, education, and communication. Hence it is paramount that such services provide the best reliability in terms of performance, features, and security to ensure the safeguarding and optimum experience for the public.
References
Achilleos, A. P., Kritikos, K., Rossini, A., Kapitsaki, G. M., Domaschka, J., Orzechowski, M., Seybold, D., Griesinger, F., Nikolov, N., Romero, D., & Papadopoulos, G. A. (2019). The cloud application modelling and execution language. Journal of Cloud Computing, 8(1). https://doi.org/10.1186/s13677-019-0138-7
Bollen, L., H., De Haes, S., Hassink Joshi, A., & Van Grembergen, W. (2018). Explaining information technology governance disclosure through the constructs of information technology governance maturity and information technology strategic role. Information & Management, 55, 368-380. https://doi.org/10.1016/j.im.2017.09.003
DesLauriers, J., Kiss, T., Ariyattu, R. C., Dang, H. V., Ullah, A., Bowden, J., Krefting, D., Pierantoni, G., & Terstyanszky, G. (2020). Cloud apps to‐go: Cloud portability with TOSCA and MiCADO. Concurrency and Computation: Practice and Experience. https://doi.org/10.1002/cpe.6093
Gholami, S., Goli, A., Bezemer, C.-P., & Khazaei, H. (2020). A framework for satisfying the performance requirements of containerized software systems through multi-versioning. Proceedings of the ACM/SPEC International Conference on Performance Engineering. https://doi.org/10.1145/3358960.3379125
Li, H., Zhang, L., Li, W., & Gao, J. (2019). A service performance based dynamic provisioning approach in containerized cloud environments. Proceedings of the 2nd International Conference on Big Data Technologies – ICBDT2019. https://doi.org/10.1145/3358528.3358568
Liu, Y., Lan, D., Pang, Z., Karlsson, M., & Gong, S. (2021). Performance evaluation of containerization in edge-cloud computing stacks for industrial applications: A client perspective. IEEE Open Journal of the Industrial Electronics Society, 2, 153–168. https://doi.org/10.1109/ojies.2021.3055901
Patni, J. C., Banerjee, S., & Tiwari, D. (2020). Infrastructure as a Code (IaC) to software defined infrastructure using Azure Resource Manager (ARM). 2020 International Conference on Computational Performance Evaluation (ComPE). https://doi.org/10.1109/compe49325.2020.9200030
Ravula, S. (2017). Achieving continuous delivery of immutable containerized microservices with Mesos/Marathon [Unpublished masters dissertation]. Aalto University.
Rios, E., Iturbe, E., & Palacios, M. C. (2017). Self-healing multi-cloud application modelling. Proceedings of the 12th International Conference on Availability, Reliability and Security. https://doi.org/10.1145/3098954.3104059
Shimizu, R., & Kanuka, H. (2020). Test-Based least privilege discovery on cloud Infrastructure as Code. 2020 IEEE International Conference on Cloud Computing Technology and Science (CloudCom). https://doi.org/10.1109/cloudcom49646.2020.00007
Xia, W., Ling, X., Wang, J., Ma, X., Wang, Z., Chen, H., Tao, L., Huang, Y., & Ye, R. (2021). Design and implementation of Docker-based image repository management system of dispatching and control cloud. 2021 IEEE 5th Advanced Information Technology, Electronic and Automation Control Conference (IAEAC). https://doi.org/10.1109/iaeac50856.2021.9390890